Recent advances in quantum computers have brought information technology one step closer to a true quantum leap in processing power. The implications are vast and massive improvements in fields as disparate as artificial intelligence and drug development will come rapidly upon their implementation. However, the ability to juggle mammoth amounts of information has also caused concern in the security world where quantum computing has the power to break into the majority of the world's encrypted information.
Quantum computers' aptitude at finding 'best' solutions to complex problems will significantly advance information processing services and research
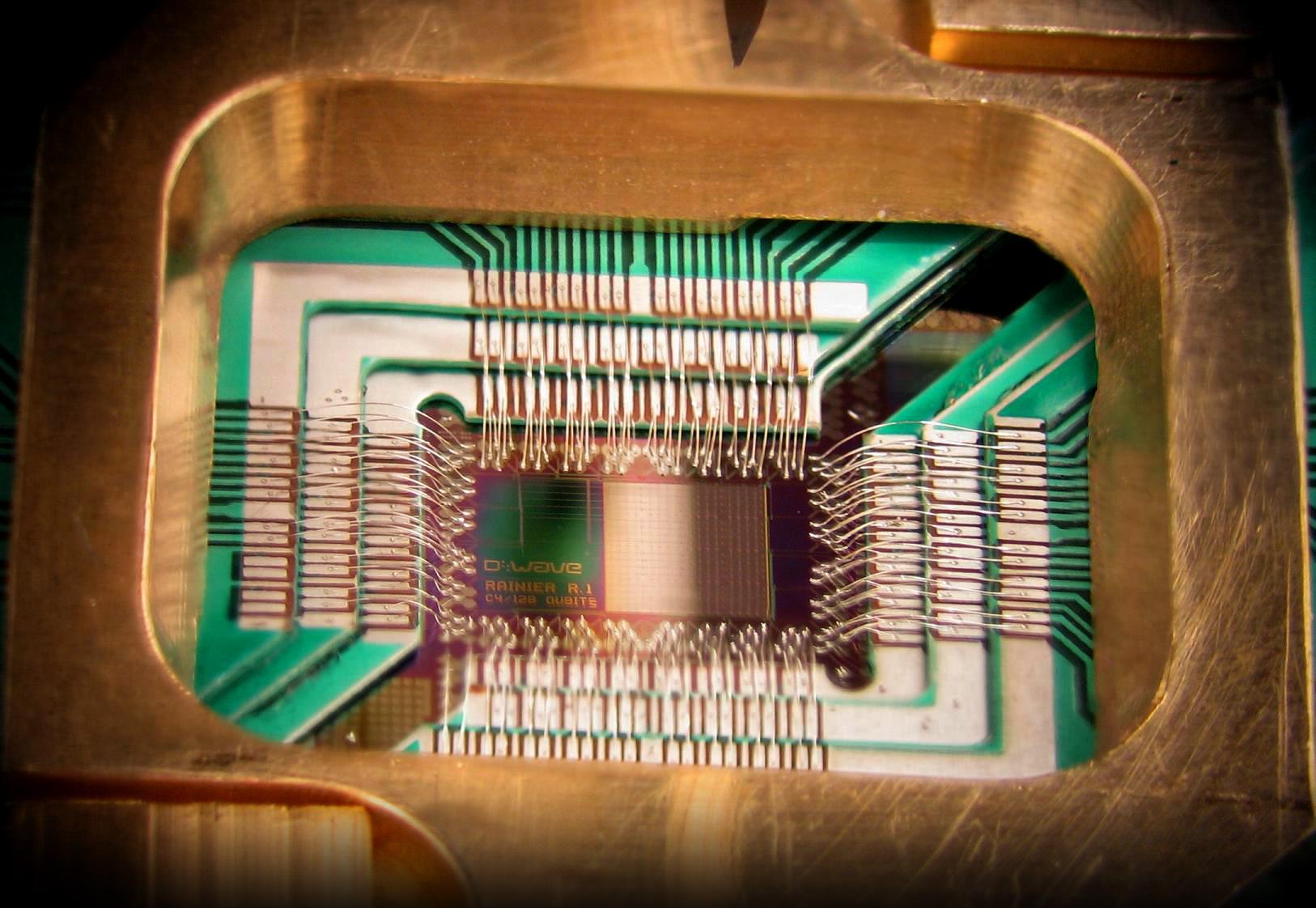 |
| D-Wave Ones, the first commercial quantum computers, were sold to Google and NASA for $10 million each Source: D-Wave Systems |
The first commercially available quantum computers (made by the company D-Wave) were quickly purchased by large companies and government entities such as Google and NASA as one means of tackling this.
The greatest driver of corporate and government interest is the search for optimal solutions. Optimization problems involve finding the 'best' solution to a problem. A problem can be finding flights to five different countries. An optimal solution would be finding the cheapest price. Many problems, however, have multiple factors competing for optimization. The 'best' series of flights, in addition to minimizing costs, would maximize comfort and limit layovers.
Considering all of these factors and more for fields such as climate modeling and drug development requires massive computing power. In the latter, protein folding modeling involves overseeing an innumerable number of interactions that is oftentimes daunting to process on a classical computer.
As the ability to accurately do so is related to the successful development of new medicines, computing power is a massive bottleneck to already expensive drug production. Professor of Physics and Quantum Computer Researcher Chris Lobb of the University of Maryland predicts that quantum computers, much more efficient than traditional computers in this regard, can greatly simplify the process.
As the ability to accurately do so is related to the successful development of new medicines, computing power is a massive bottleneck to already expensive drug production. Professor of Physics and Quantum Computer Researcher Chris Lobb of the University of Maryland predicts that quantum computers, much more efficient than traditional computers in this regard, can greatly simplify the process.
The timeline of quantum computer development is subject to financial forces. Lobb states that the pace of commercial computer development will hinge primarily on corporate interest. Depending on the value companies place on quantum computers, he says, we may be able to see the computers in commercial action in as soon as five to ten years.
Ability for quantum computers to break popular methods of encryption likely to cause widespread change in how information is protected
The development of quantum computers is not without potential problems. A large scale quantum computer introduced today would wreak unfathomable havoc on the world. The computational power of a quantum computer would possess the ability to crack open secret information like an egg. The vast majority of the secured, private information on the internet would become ripe for harvest. Lobb predicts that it would likely result in the collapse of the world's financial markets.
Popular social media websites such as Facebook and Twitter as well as financial entities such as banks make extensive usage of a form of encryption known as RSA. With RSA, websites can send, receive, and store private information without reasonable fear that a third party will steal it. Its popularity is due mostly to the fact that reliably breaking through RSA takes too long for classical computers to reliably break. However, quantum computers have the power to make quick and consistent decryption a reality.
The quantum computer's importance in information security can be easily seen in the National Security Agency's marked interest in the technology. Recent leaks by Edward Snowden have shown the vast extent of the agency's data collection efforts. The ability to achieve quantum computing capability allows the agency to both gather data before encryption is updated as well as undertake the measures necessary to safeguard its own data. To that end, it has invested around $80 million on both public and classified quantum computing research projects.
However, there exists a number of encryption methods that will not crumble in the midst of quantum computers. Methods such as Hash-based cryptography and Code-based cryptography have proven thus far to be resistant to both classical and quantum means of encryption breaking.
The only advantage RSA possesses over alternative means of encryption is efficiency (it takes less processing to produce the same security). As the threat of a quantum computer becomes more and more real, the efficiency consideration is likely to give way to a transition to more secure encryption systems.
The only advantage RSA possesses over alternative means of encryption is efficiency (it takes less processing to produce the same security). As the threat of a quantum computer becomes more and more real, the efficiency consideration is likely to give way to a transition to more secure encryption systems.
Quantum computers use quantum mechanical phenomena to store more information with less resources than traditional computers
Understandably, the difference between quantum and traditional computers may seem fairly insignificant on the surface. After all, reductions in the size and increases in the number of computer chips we see so much right now also contributes to improvements in computing power and it would be easy to think that quantum computers are just another rung on this developmental ladder. However, it is important to recognize that quantum computers deviate from classical computers fundamentally in the way information is stored and handled.
Traditional computers handle information in packets called 'bits'. The bit consists of one piece of information expressed as either a one or a zero. This is manifested physically through electronic 'gates' that permit or restrict the flow of electricity in a computer, respectively. One value is enough to describe the state of a gate and thus each gate only contains one value's worth of information.
A quantum computer reads information in what are known as quantum bits or 'qubits'. Like traditional bits, qubits store information through a two state system. However, qubits can take advantage of a quantum mechanical property known as 'superposition'.
On the scale where quantum mechanics dominates (less than the size of an atom), a particle can be in a combination or superposition of two states at one time. In other words, a particle that can spin in two different ways can be spinning a little bit in one way and a little bit in the other. Quantum computers uses these particle superposition packets as its qubits.
On the scale where quantum mechanics dominates (less than the size of an atom), a particle can be in a combination or superposition of two states at one time. In other words, a particle that can spin in two different ways can be spinning a little bit in one way and a little bit in the other. Quantum computers uses these particle superposition packets as its qubits.
The information storage advantage in qubits is clear. Whereas the bit can only contain the information 'one' or 'zero', the qubit can contain "how much one" and "how much zero". There are two values required to describe each qubit and thus there are two values contained within each qubit, twice the amount of information contained for each bit. Scaling this up to more bits, each additional bit doubles the amount of information held in the system relative to traditional bits in exponential fashion.
 To understand this in familiar terms, imagine that you are a pizza lover disappointed in the inconsistency of the pizzas you receive. Currently, you describe the pizzas you want with your choice of topping: pepperoni. With this description, the pizza either has or does not have pepperoni.There is no in-between. The order has the information of one classical bit that can be either a one or zero but not both.
To understand this in familiar terms, imagine that you are a pizza lover disappointed in the inconsistency of the pizzas you receive. Currently, you describe the pizzas you want with your choice of topping: pepperoni. With this description, the pizza either has or does not have pepperoni.There is no in-between. The order has the information of one classical bit that can be either a one or zero but not both.
However, this method of description always falls short. The pizzas you receive always have the maximum number of pepperonis- too many pepperonis for your cultivated taste! One bit simply does not contain enough information to fully describe the ideal pepperoni saturation.
Luckily, you devise a new method of ordering pizzas. Next time, you order your pizza while mentioning a precise amount of pepperoni. It is obvious that more information is being communicated. In fact, the amount of information communicated is precisely doubled.
The speed of computation is directly related to the number of steps needed to complete it. Because qubits contain exponentially more information than bits, a quantum computer can complete the tasks of a classical computer with much fewer calculations. Indeed, whereas a traditional computer would need an unfathomable amount of bits to model the observable universe (one for each particle), a quantum computer could model it with just 400. If quantum bits can be read as quickly as traditional bits, this exponential advantage in calculations is also an exponential advantage in speed.
RSA encryption relies on the difficulty of prime factorization for security which quantum computers easily circumvent
Fundamentally, RSA encryption revolves around two very large prime numbers. Prime numbers are numbers whose only factors (numbers that divide them evenly) are themselves and one. These numbers are multiplied to create an even larger value with only the two numbers as factors. The encryption works on the premise that it is very difficult to find the factors of very large numbers. Indeed, for sufficiently large numbers, traditional methods of decryption would take more than the lifetime of the universe to complete.
 Traditional methods of prime factorization require calculations that increase exponentially with the size of the number. However, quantum computers can break the encryption in what is known as polynomial time. Compared to exponential time, polynomial time is vastly more expedient. As a result, they can break encrypted message with significantly fewer calculations. Data that is safe to classical computers may not be safe to quantum computers.
Traditional methods of prime factorization require calculations that increase exponentially with the size of the number. However, quantum computers can break the encryption in what is known as polynomial time. Compared to exponential time, polynomial time is vastly more expedient. As a result, they can break encrypted message with significantly fewer calculations. Data that is safe to classical computers may not be safe to quantum computers.Isolation, algorithm writing, scalability, precision, and verification of true quantum computing are some of the obstacles to a functional quantum computer
The greatest obstacle to a large scale quantum computer, says Lobb, is the maintenance of the quantum computing environment. The quantum superposition state of a system is inherently fragile. The smallest interaction with the outside environment can take the system out of superposition. The problem of isolation is magnified by the intrinsic involvement of interaction in reading and writing data from and to a system.
Numerous other factors stand in the way of successful quantum computing. For example, quantum algorithms are much more difficult to formulate than traditional ones. Very few algorithms exist that permit a quantum computer from truly outperforming a comparable classical computer.
In addition, it is extremely difficult to scale quantum computers up to a functional size. Rudimentary quantum computers exist but can do little more than trivial calculations that can be done much more quickly on classical computers.
Qubits also demand much more precision of measurement. Whereas bits can only be up or down, qubits can be in a superposition and the exact amount of up and down is extremely pertinent to the reliability of a quantum calculation.
Problems also exist in verifying if existing computers truly employ quantum computing principles. Upon the announcement of D-Wave's D-Wave One quantum computer, there was significant controversy surrounding the computer's use of quantum mechanics.
Initial benchmarking conducted by NASA and Google showed improvements of up to 3600 times greater speeds in certain software applications. However, tests undertaken by independent researchers demonstrated a lack of improvement over conventional computer and questioned if quantum principles were being employed.
Despite these barriers, quantum computer development marches ahead at a strong pace. Before we know it, quantum computers might become an integral part of the technological world.
Initial benchmarking conducted by NASA and Google showed improvements of up to 3600 times greater speeds in certain software applications. However, tests undertaken by independent researchers demonstrated a lack of improvement over conventional computer and questioned if quantum principles were being employed.
Despite these barriers, quantum computer development marches ahead at a strong pace. Before we know it, quantum computers might become an integral part of the technological world.
No comments:
Post a Comment